





Published on Mar 01, 2025
This paper presents an technique that is enhanced for the basic CCTV cameras which can automatically detect the abandoned luggage through the pre used CCTV camera, for detection we are using background subtraction technique and foreground object extraction .where all the image extracted from the CCTV surveillance is classified as 2 bit code and identify static foreground region, and identifying the abandoned object.
This technique is basically introduced for making the public places safe and secure where abandoned object may have weapons bombs and many other harmful equipments.
As it is the crucial task to have a public safety all over public places many bomb attacks are held all over country so as the main motive of a bomber is to place the bomb in public places so this technique helps us to detect the placed object and providing an alarm to the CCTV monitor which can help to avoid this situation hence we are using background subtraction technique which is suitable for object detection and recognizing the static foreground, the pre-processing involves a dual-time background removal algorithm which vigorously updates two sets of background, one after a very short intervals (less than a half seconds) and the other relatively longer duration. The agenda of proposed algorithm is based upon the Imprecise Median Model.an algorithm for tracing of abandoned objects even under occlusion is also proposed. Results show that the system is tough to variations in lighting.
The basic CCTV camera is been used all over the world so the system can be implemented easily to all over CCTV, this system is been also used on the army borders, but not into the public places such as metro station big malls shops, so this can be used where people gather more to the places and also as a security to avoid this massacre, as the normal CCTV cameras track the situation and after the incident is occurred so avoid this incident we have proposed this system. Which has an continuous monitoring of the abandoned object and detection alarm after some span of time. This can save many people‘s lives by adapting this new technique, This Technique is only used in army borders; this can be adapted in our day to day public places for security.
We are processing the live feed of CCTV camera with the image processing. If a person is releasing off some piece of luggage or any such doubtful thing leaving it running away the camera will catch the activity. If the bag is untouched for a some period of time the analyser decides and further gives an alarm to the authority. Minimum the time span the possibility stays but as the probability if that thing being abandoned or hazardous increases. Hence the incident can be avoided in this case.
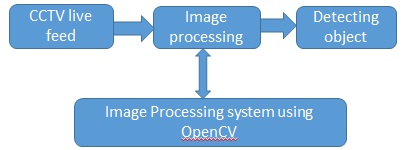
The CCTV takes the live feed and this frames are been detected and been image processed by background subtraction. Where the background is eliminated and object is only focused this elimination and processing is done by the OpenCV which is a platform independent library used for image processing which detects the abandoned object and sets an alarm and alerts the authority. This technique of object framing is used in most high quality cameras know as face detection. Using this similar technique we can detect the abandoned luggage
Let ‗S‘ be the | Abandon Object detectionas the final set
S = {…………}
Identify the inputs as I S = {V}
V = {V1, V2, V3, V4 …| 'V‘ given video captured from camera} Identify the outputs as O
S = {AR, DO}
DO= {DO1, DO2, DO3 …| 'DO‘ given Detected object}
AR = {AR1, AR2, AR3 … | 'AR' gives the alert report}
Identify the functions as ‗F
‘ S = {…
F = {F1 (), F2(), F3(), F4(), F5(), F6(), F7()}
F1 (V) :: Capture video from camera
F2 (V) :: divide it into frame .
F3 (V) :: image processing.
F4 (V) :: detect object
F5 (V) :: analysis and monitoring for particular time.
F6 (V) :: generate alert
F7 (V):: Send alert report to the system
OpenCV (Open Source Computer Vision Library) is an open source computer idea and machine learning software public library. OpenCV was manufactured to provide a common structure for computer image applications and to hasten the use of machine view in the commercial products. Being a BSD-licensed product, OpenCV makes it easy for productions to operate and modify the code. The library has more than 2500 elevated algorithms, which includes a broad set of both classic and state-of-the-art computer idea and machine learning algorithms.
These algorithms can be used to perceive and distinguish faces, identify objects, organize human actions in videos, track camera arrangements, track moving objects, extract 3D models of items, produce 3D point clouds from stereo cameras, stitch images collected to produce a high resolution image of an complete scene, find comparable images from an image database, remove red eyes from images taken using flash, follow eye activities, recognize scenery and formindicators to overlay it with augmented reality, etc. OpenCV has more than 47 thousand people of user communal andpredictable number of downloads above 7 million. The library is usedbroadly in companies, research groups and by governmental bodies.
The query image is the method through which the OpenCV should perform where OpenCV can perform various different task of image processing hence we are using the back-tracing technique where background image is subtracted and foreground image is traced.
The particular task is been extracted and only the following task is been activated that is query processing acquired by the user.
The query which is been given by the user is been checked before the processing into the database and if the query is new it is stored into the database and then it is further performed.
A Java Virtual Machine (JVM) is a customary of computer software programs and data structures that use a virtual machine exemplary for the execution of supplementary computer programs and scripts. The model used by a JVM admits a form of computer transitional language commonly referred to as Java byte code. This language nearly represents the instruction set of a stack-oriented, capability style. Java Virtual Machines function on Java byte code, which is normally (but not necessarily) created from Java source code; a JVM can also be used to tool programming languages other than Java. The JVM is a vital component of the Java Platform. Because JVMs are available for numerous hardware and software platforms, Java can be together middleware and a platform in its own accurate—hence the trademark transcribe once, run anywhere. The use of the similar byte code for all plat-forms badges Java to be labelled as‖ compile once, run anywhere‖, as divergent to‖ write once, compile anywhere‖, which defines cross-platform compiled languages. The JVM also empowers such features as Automated Exception Handling that delivers ‘root-cause‘ debugging information for each software error(exception) sovereign of the source code.
We have proposed a scheme by progressivereliability model combining a back-tracing algorithm for abandoned object detection. by back-tracing algorithm iteratively paths the luggage owner by using spatial-temporal windows to efficiently verify left-luggage events. The image processing takes minimum of NP COMPLETE Of Time. Our back-tracing algorithm iteratively tracks the luggage owner by using spatial-temporal windows to efficiently verify left-luggage events.
[1] ―A survey on visual surveillance of object motion and behaviors,‖H. Weiming, T. Tieniu, W. Liang, and S. Maybank, IEEE Trans. Syst., Man, Cybern. C, Appl. Rev., vol. 34, no. 3, pp. 334–352, Aug. 2004.
[2] ―Active video-based surveillance system: The low-level image and video processing techniques needed for implementation,‖G. L. Foresti, C. Micheloni, L. Snidaro, P. Remagnino, and T. Ellis IEEE Signal Process. Mag., vol. 22, no. 2, pp. 25–37, Mar. 2005
[3] ―Tracking-based event detection for CCTV systems,‖ L. M. Fuentes and S. A. Velastin, Pattern Anal. Appl., vol. 7, no. 4, pp. 356–364, Dec. 2004.
[4] N. Firth, Face recognition technology fails to find U.K. rioters, NewScientist, London, U.K. [Online]. Available: http://www.newscientist. com/article/mg21128266.000-face-recognition-technology-fails-to-finduk-rioters.html
[5] ―A real time semantics-based detection of suspicious activities in public scenes,‖M. Elhamod and M. D. Levine, in Proc. 9th Conf. CRV, Toronto, ON, Canada, 2012, pp. 268–275.