





Published on Mar 01, 2025
Everyday almost 20 million of installs [1], minor-party apps are a main reason for the popularity and obsess of facebook. Disastrously, hackers have registered the possibility of using apps for extending malware and spam. The issue is already valid, as we find that at least 13% of apps in our dataset are malicious. So far, the research center has concentrated on detecting malicious posts and campaigns. In this paper, we ask the question: Given a facebook application, can we figure out if it is malicious? Our main contribution is in evolving FRAppE—Facebook’s Rigorous Application Evaluator—feasibly the first tool focused on detecting malicious apps on facebook.
To implement FRAppE, we use data gathered by monitoring the posting action of 111K facebook apps [2] seen across 2.2 million users on facebook. Initially, we determine a set of features that help us classify the malicious apps from favorable ones. For instance, we figured it out that malicious apps frequently share names with other apps, and they generally seek fewer permissions than favorable apps. Secondly, leveraging these characterizing features, we present that FRAppE can encounter malicious apps with 99.5% precision, with no false positives and a elevated true positive rate (95.9%).
Finally, we scrutinize the ecosystem of malicious facebook apps and find mechanisms that these apps use to generate. Fascinatingly, we identify that many apps collaborate and assist each other; in our dataset, we identify 1584 apps facilitating the viral proliferation of 3723 other apps across their posts. Long term, we notice FRAppE as a step forward building an independent protector for app appraisal and grading, so as to alert Facebook users before installing apps.
Online social networks (OSNs) allows and encourages the third-party apps (applications) to improve the user experience on these forums. Such enhancements include fascinating or amusing ways of interacting among online friends and different activities such as playing games or listening to songs. For instance, facebook supplies creator’s an API that enables app merger into the Facebook user experience. There are five hundred thousand apps accessible on Facebook, and in generally, twenty million apps are installed regularly. Further-more, numerous apps have procured and continue a really large access provider.
For instance, Farmville and Cityville apps have 26.5million and 42.8million users to date. A short time ago, hackers began gaining benefit of the reputation of this third-party apps forum and install malicious applications. Malicious apps can supply a profitable career for hackers, given the popularity of OSNs, with facebook leading the way with nine hundred million active users. There are numerous ways that hackers can gain from a malicious app:
1) The app can attain large numbers of users and their friends to propagate spam
2) The app can grab users personal information such as e-mail address, hometown, and gender,
3) The app can ―generate‖ by making variant malicious apps well liked.
To make matters deffective, the deployment of malicious apps is simplified by ready-to-use toolkits starting at $25. In other words, there is purpose and possibility, and as a result, there are various malicious apps propagating on facebook daily.
Malicious Web sites are the foundation of Internet criminal activities. Correspondingly, there has been immense interest in implementing methods to forbid the end user from visiting such sites. In this paper, a technique is characterized for this issue based on automated URL classification, using statistical aproaches to identify the tell-tale lexical and host-based properties of malicious Web site URLs. These methods are able to grasp highly predictive models by extracting and automatically determining ten thousands of characteristics probably demonstrative of suspicious URLs.
The resulting classifiers acquire 95-99% precision, identifying large numbers of malicious Web sites from their URLs, with only modest false positives. This was referred from J. Ma, L. K. Saul, S. Savage, and G. M.Voelker beyond blacklists: Learning to detect malicious Web sites from suspicious URLs, K. Thomas, C. Grier, J. Ma, V. Paxson, and D. Song was said that Design and evaluation of a realtime URL spam filtering service, On the heels of the comprehensive selection of web services such as social networks and URL shorteners, scams, phishing, and malware have become regular dangers. Although broad research, email-based spam filtering methods basically fall short for guarding other web services.
To better represent this need, we show Monarch, a real-time system that crawls URLs as they are submitted to web services and checks whether the URLs direct to spam. We assess the viability of Monarch and the basic challenges that occur due to the difference of web service spam. We present that Monarch can supply exact, real-time protection, but that the basic features of spam do not conclude across web services. In particular, we identify that spam aiming on email qualitatively varies in important ways from spam campaigns targeting Twitter.
We analyze the differences between email and Twitter spam, as well as the abuse of public web hosting and redirector services. Finally, we display Monarch's scalability, showing our system could protect a service such as Twitter--which needs to process 15 million URLs/day--for a bit under $800/day. G. Stringhini, C. Kruegel, said that, the Detecting spammers on social networks, Social networking has become a popular way for users to meet and communicate online. Users spend a heavy amount of time on famous social network platforms (such as Facebook, MySpace, or Twitter), storing and sharing a wealth of personal details. This information, in addition to the possibility of interacting thousands of users, also enchant the interest of cybercriminals. For example, cybercriminals might attain the complete trust relationships among users in order to attract victims to malicious websites.
As another example, cybercriminals might find personal information valuable for identity theft or to drive targeted spam campaigns. By this paper, we analyze to which extent spam has entered social networks. More precisely, we analyze how spammers who target social networking sites operate. To collect the data about spamming activity, we created a large and diverse set of "honey-profiles" on three large social networking sites, and logged the kind of contacts and messages that they received. We then analyzed the collected data and identified anomalous behavior of users who contacted our profiles.
Based on the analysis of this behavior, we developed techniques to detect spammers in social networks, and we aggregated their messages in large spam campaigns. Our results show that it is possible to automatically identify the accounts used by spammers, and our analysis was used for take-down efforts in a real-world social network. More precisely, during this study, we collaborated with Twitter and correctly detected and deleted 15,857 spam profiles.
Detecting Spam on OSNs: Gao et al. [5] analyzed posts on the walls of 3.5 million facebook users and revealed that 10% of links posted on Facebook walls are spam. They also presented techniques to identify compromised accounts and spam campaigns. In other work, Gao et al. and Rahman et al.[6] Develop efficient techniques for online spam filtering on OSNs such as Facebook. While Gao et al. [5] rely on having the whole social graphs input, and so is usable only by the OSN provider, Rahman et al. develop a minorparty application for spam detection on facebook. Others present mechanisms for detection of spam URLs on Twitter.
In contrast to all of these efforts, rather than classifying individual URLs or posts as spam, we focus on identifying malicious applications that are the main source of spam on Facebook. Detecting spam accounts. Yang et al. [7] and Benevenuto et al. developed techniques to identify accounts of spammers on Twitter. Others have proposed a honey-pot-based approach to detect spam accounts on OSNs. Yardi et al. analyzed behavioral patterns among spam accounts in Twitter. Instead of focusing on accounts created by spammers [8], our work enables detection of malicious apps that propagate spam and malware by luring normal users to install them.
As yet, the research center has paid a bit notice to OSN apps particularly. The majority of research associated to spam and malware on Facebook has concentrated on identifying malicious posts and social spam campaigns. Gao et al. surveyed posts on the walls of 3.5 million Facebook users and revealed that 10% of links posted on Facebook walls are spam. They also demonstrated methods to find compromised accounts and spam campaigns. Yang et al. and Benevenuto et al. implemented approaches to determine accounts of spammers on Twitter. Others have introduced a honey-pot-based method to identify spam accounts on OSNs. Yardi et al. surveyed behavioral patterns between spam accounts in Twitter. Chia et al. scrutinize risk signaling on the privacy intrusiveness of Facebook apps and negotiate that present forms of community ratings are untrustworthy indicators of the privacy risks related with an app.
In this paper, we implement FRAppE, a suite of well organized sort of techniques for recognizing whether an app is malicious or not. To design FRAppE, we utilize data from MyPage-Keeper, a security app in facebook. We identify that malicious applications notably vary from favourable applications followed by two types of classes: On-Demand Features and Aggregation-Based Features. We present two forms of our malicious app classifier— FRAppE Lite and FRAppE. FRAppE Lite is a lightweight version that makes employs of only the application characteristics accessible on demand. Given a precised app ID, FRAppE Lite crawls the on-demand characteristcs for that application and assess the application based on these features in real time. FRAppE is a malicious app detector that employs our aggregation-based features besides the on-demand features.
The proposed work is probably the first inclusive research aiming on malicious Facebook apps that concentrates on quantifying, profiling, and understanding malicious apps and integrates this data into an beneficial detection approach. Various characteristics used by FRAppE, such as the status of redirect URIs, the number of required permissions, and the utilization of different client IDs in app installation URLs, are durable to the development of hackers. Not using different client IDs in app installation URLs would bound the potential of hackers to instrument their applications to spread each other.
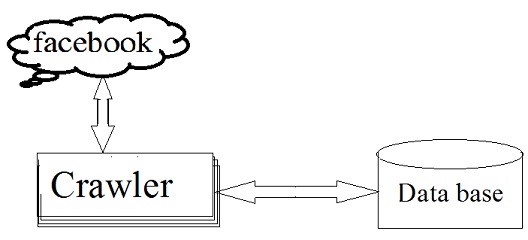
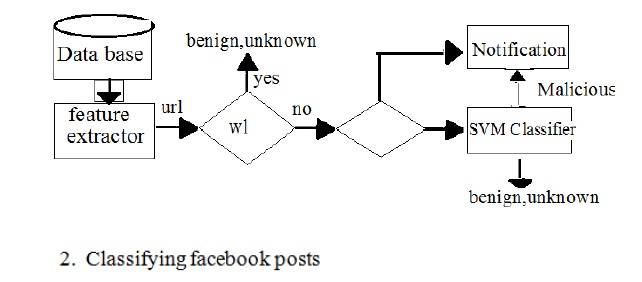
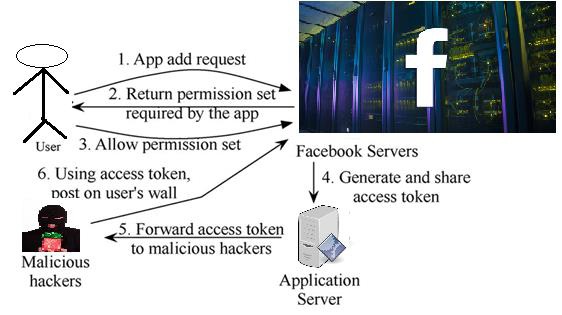
Operation of Malicious Applications: Malicious Facebook applications typically operate as follows. Hackers will convince users to install the application, usually with some fake promise (e.g., free mobiles). Once a user installs the app, it redirects the user to a web page where the user is asked to perform tasks, such as completing a survey, again with the lure of fake rewards. The app thereafter accesses personal information (e.g.,birthdate) from the user’s profile, which the hackers can potentially use to profit. The app makes malicious posts on behalf of the user to lure the user’s friends to install the same app (or some other malicious app, as we will see later). This way the cycle continues with the app or colluding apps reaching more and more users. Personal information or surveys can be sold to third parties[4] to eventually profit the hackers.
Applications present convenient means for hackers to spread malicious content on facebook.. In this paper, using a large corpus of malicious facebook apps observed over a nine-month period, we showed that malicious apps differ significantly from benign apps with respect to several features. For example, malicious apps are much more likely to share names with other apps, and they typically request fewer permissions than benign apps. Leveraging our observations, we developed FRAppE, an accurate classifier for detecting malicious Facebook applications. Most interestingly, we highlighted the emergence of app-nets large groups of tightly connected applications that promote each other. We will continue to dig deeper into this ecosystem of malicious apps on facebook, and we hope that facebook will benefit from our recommendations for reducing the menace of hackers on their platform.
1. C.Pring, ―100 social media statistics for 2012,‖2012 [Online]. Available: http://thesocialskinny.com/100- social-media-statistics-for-2012/.
2.―My PageKeeper,‖ [Online]. Available: https://www.facebook.com /apps/application. php? id= 167087893342260.
3. F.J.Damerau, ―A technique for computer detection and correction of spelling errors, ‖Commun. ACM,vol.7,no.3,pp.171–176, Mar.1964.