





Published on Mar 01, 2025
Positioning misrepresentation in the portable Application business shows to false or dubious activities which have a motivation behind, thumping up the Applications in the popularity list. To be sure, it ends up being more endless for Application architects to adventure shady means, for instance, developing their Applications' business or posting fraud Application assessments, to ponder situating deception. While the ramification of abstaining from positioning misrepresentation has been by and large maintained, there is constrained comprehension and examination here.
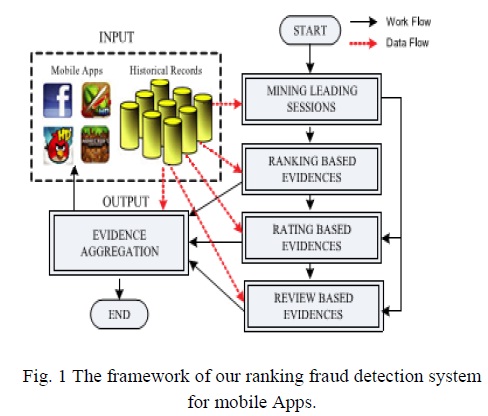
This paper gives an all-inclusive viewpoint of situating deception and proposes a Positioning misrepresentation distinguishing proof structure for versatile Applications.
In particular, it is proposed to precisely discover the mining in order to posture blackmail the dynamic periods, to be particular driving sessions, of compact Applications. Such driving sessions can be used for recognizing the area irregularity as opposed to an overall anomaly of Application rankings. In addition, three sorts of verification s are investigated, i.e., situating based affirmations, displaying to rate based confirmations and study based evidences, Applications' situating, rating and review rehearses through genuine speculations tests. In the request, this paper gets the skill of the proposed system, and shows the distinguishing proof's flexibility estimation furthermore some consistency of situating deception works out.
The amount of compact Applications has created at a stunning ate over the span of late years. For example, as of the end of April 2013, there are more than 1.6 million Applications at Apple's Application store and Google Play. To invigorate the change of adaptable Applications, various Application stores pushed each day Application pioneer sheets, which display the blueprint rankings of most pervasive Applications.
As a general rule, the Application pioneer board is a champion amongst the most fundamental courses for progressing flexible Applications. A higher rank on the pioneer board generally prompts an epic number of downloads and million dollars in salary. Thus, Application architects tend to research diverse courses, for instance, publicizing push to propel their Applications to have their Applications situated as high as could be normal in light of the current situation in such Application pioneer sheets. Then again, as a late example, instead of relying upon standard advancing game plans, shady Application engineers resort to some tricky expects to intentionally bolster their Applications and over the long haul control the chart rankings on an Application store.
This is regularly executed by using gathered "bot farms" or "human water military" to swell the Application downloads, examinations and studies in a brief time span. Case in point, an article from Endeavor Beat reported that, when an Application was progressed with the help of situating control, it could be moved from number 1,800 to the fundamental 25 in Apple's sans top pioneer board and more than 50,000-100,000 new customers could be increased within a couple of days. Honestly, such situating blackmail raises marvelous stresses to the flexible Application industry. Case in point, Apple has advised of making a move against Application architects who submit situating deception in the Apple's Application store.
In this paper, developed a situating coercion distinguishing proof structure for flexible applications that situating distortion happened in driving sessions for every application from its obvious situating records.
In this strategy, we address the issue of study spammer acknowledgment, or ding customers who are the wellspring of spam reviews. Not at all like the techniques for spammed study acknowledgments, our proposed review spammer area procedure is customer driven, and customer behavior driven. A customer driven technique is favored over the review driven strategy as social event behavioral verification of spammers is less requesting than that of spam reviews.
In this paper we first give a general framework for coordinating Regulated Rank Accumulation. We show that we can describe coordinated learning methods identifying with the current unsupervised systems, for instance, Board Check what's more, Markov Chain based schedules by mishandling the framework. By then we overwhelmingly explore the regulated types of Markov Chain based systems in this paper, in light of the way that past work shows that their unsupervised accomplices are unrivaled. All things being equal turns out, then again, that the streamlining issues for the Markov Chain based schedules are hard, in light of the way that they are not bended change issues.
In this paper, creator demonstrated various sorts of conventions to protect the protection or security of the information. This paper contemplated the issue of centrality sparing in MANETs in context of the system for structure coding and displayed that System Coding is valuable in figuring, and gets less significance use for encryptions/decodings.
We first propose a straightforward yet viable calculation to distinguish the main sessions of each Application in view of its authentic positioning records. At that point, with the investigation of Applications' positioning practices, we find that the fake Applications frequently have distinctive positioning examples in every driving session contrasted and ordinary Applications. In this way, we portray some misrepresentation confirmations from Applications' authentic positioning records, and create three capacities to concentrate such positioning based extortion confirmations. We facilitate propose two sorts of misrepresentation proofs in light of Applications' appraising and survey history, which mirror some irregularity designs from Applications' verifiable rating and audit records.
By breaking down the Applications' verifiable positioning records, we watch that Applications' positioning practices in a main occasion dependably fulfill a particular positioning example, which comprises of three distinctive positioning stages, in particular, rising stage, keeping up stage and subsidence stage.
2). Rating Based Confirmations: Particularly, after an Application has been distributed, it can be evaluated by any client who downloaded it. To be sure, client rating is a standout amongst the most essential components of Application ad. An Application which has higher rating might pull in more clients to download and can likewise be positioned higher in the leader board. Subsequently, evaluating control is likewise a vital point of view of positioning misrepresentation.
Other than evaluations, the vast majority of the Application stores additionally permit clients to compose some printed remarks as Application audits. Such audits can mirror the individual observations and use encounters of existing clients for specific portable Applications. Surely, survey control is a standout amongst the most critical viewpoint of Application positioning misinterpretation.
By dissecting the authentic positioning records of mobile Apps, we watch that Applications are not generally positioned high in the leader board, but rather just in some driving occasions. Besides, we likewise find that a few Applications have a few nearby driving occasions which are near one another and structure a main session. For instance, Fig. 2b demonstrates an illustration of neighboring driving occasions of a given mobile Application, which shape two driving sessions.
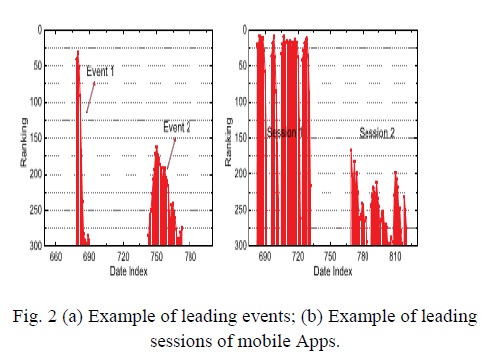
The positioning based proofs are valuable for positioning extortion location. Be that as it may, once in a while, it is not adequate to just utilize positioning based proofs. For instance, a few Applications made by the renowned engineers, for example, Diversion space, might make them lead occasions with substantial estimations of because of the designers' believability and the "informal "publicizing impact.
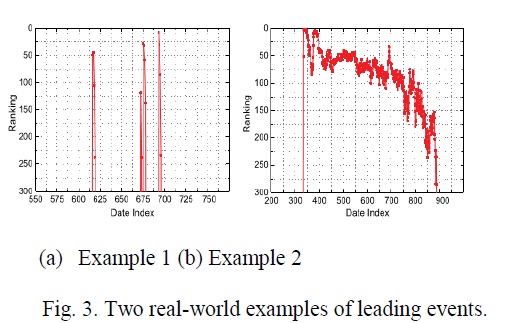
Besides, a percentage of the legitimate advertising administrations, for example, "constrained time rebate", might likewise bring about huge positioning based confirmations. To tackle this issue, we additionally concentrate how to concentrate extortion confirmations from Applications' authentic rating records. Accordingly, we ought to first investigate the essential attributes of driving occasions for separating misrepresentation confirmations. By dissecting the Applications' authentic positioning records, we watch that Applications' positioning practices in a main occasion dependably fulfill a particular positioning example, which comprises of three the diverse positioning stages, to be specific, pising stage, keeping up stage and retreat stage. In particular, in every driving occasion, an Application's positioning first increments to a crest position in the pioneer board (i.e., rising stage), then keeps those such crest position for a period. Fig.3 demonstrates an illustration of various positioning periods of a main occasion. TIndeed, such a positioning example demonstrates a critical comprehension of driving occasion. In the accompanying, we formally characterize the three positioning periods of a main occasion.
Besides, to recognize the positioning extortion from a few driving sessions, an intuitive methodology is created termed as Proof Collection based Positioning Misrepresentation Location (EA-RFD). Especially, this methodology is meant with score based conglomeration (i.e., Rule 1) as EA-RFD-1, and methodology with rank based collection (i.e., Standard 2) as EARFD-2, separately. In the underneath Fig, there exist a seven free Applications which may include in positioning extortion to be specific as Small Pets, Social Young lady, Cushion Companions, Wrongdoing City, VIP Poker, Sweet Shop, Top Young lady. So every methodology like EA-RFD1 and EA-RFD2 is connected on these Applications to locate the suspicious Applications with high positioning. Subsequent to a decent positioning based identification framework is worked to distinguish extortion Applications from a given dataset of portable Applications. Henceforth by every methodology given in Fig.4, top rate position of each Application in the positioned rundown is distinguished.
So as to study the execution of positioning extortion discovery by every strategy, we set up the appraisal as takes after. To start with, for every technique, we named 50 top positioned driving sessions (i.e., most worried sessions), 50 center positioned driving sessions (i.e., most uncertain sessions), and 50 base positioned driving sessions (i.e., most ordinary sessions) from every information set. At that point, we consolidated all the chose sessions into a pool which comprises 587 special sessions from 281 exceptional Applications in "Top Free 300" information set, and 541.
This paper introduces a framework which is developed and it is really a situating crushing revelation system for portable Applications. In particular, basically it is affirmed that situating distortion happened in driving sessions and gave a framework to exhuming driving sessions for each Application from its chronicled situating records. By then, it is perceived that situating based affirmations, rating based evidences and overview based affirmations are utilized for distinguishing situating blackmail. What's more, a remarkable model is proposed which is a change based aggregate framework to coordinate each one of the evidences for evaluating the legitimacy of driving sessions from convenient Applications..
[1] Discovery of Ranking fraud for mobile apps. Hengshu Zhu,Hui Xiong,Senior members,IEEE,Yong Ge, and Enhong Chen,Senior member,IEEE,IEEE transactions on knowledge and data engineering, vol .27, No.1, January 2015.
[2] Detecting product review spammers using rating behaviors. E.-P. Lim, V.-A. Nguyen, N. Jindal, B. Liu, and H. W. Lauw. In Proceedings of the 19th ACM international conference on Information and knowledge management.
[3] Supervised rank aggregation. Y.-T. Liu, T.-Y. Liu, T. Qin, Z.-M. Ma, and H. Li in Proceedings of the 16th international conference on World Wide Web.