





Published on Mar 01, 2025
With the advancement in networking services, network security has become the key facet in our digital world. The term network security constitutes prevention of network and network resources by ceaseless monitoring and thereby denying the services like user access to network resources and modification of network configuration details from unauthorized users. Firewalls are one such network security system that monitors the inbound and outbound traffic of the network, this observation relies on two principal factors, Stateless and Stateful firewalls.
The Stateless firewalls track the source and destination address of every incoming and outgoing data packets whereas the Stateful firewalls track each packet in the network by reading the entire header and thus it can read the type of data being transmitted. “PLUTO – A home office firewall” is a stateless firewall which can be used in Linux environment. The main motto behind developing the PLUTO as real time firewall is to demonstrate a real-time application for home office users through which they can secure their network.
Firewall and Intrusion Detection System (IDS) are the most important components of network perimeter security. [1]. Firewalls are one such network security systems that stand as a barrier through which the entire network traffic is to be passed. A firewall security policy describes which traffic is to be accepted into the network and which traffic is to be denied [2]. In general a firewall can filter the packets at IP packets similarly if needed firewalls can also be implemented at higher layers of the communication system. Firewalls are generally made to allow authorized traffic (packets that satisfy all the firewall security rules) into the network and deny rest of the traffic. PLUTO allows the system administrators to define rules for the treatment of incoming and outgoing data packets of the network. This tool uses a tree-based approach replacing existing listed rule.
Firewalls are barriers between us and rest of the world and PLUTO is one such firewall. we know that computers are connected to the internet by ports [3] (like port number 80 for HTTP traffic, port number 110 for receiving mails-pop3, port number 25 is typically used for sending mail-SMTP). The basic idea behind the implementation of firewall PLUTO is to close the unnecessary ports, if such ports are not closed, then there is no doubt in saying that this is an open invitation for hacking incidents.
a. Hacking into the network through open parts: If in a network open port exists then it’s known as a security breach due to which someone can intrude into our network and may cause information loss.
b. Hacking as harmless network interaction in our network: If we don’t have any firewall in our network crackers may intrude into the network and may alter the networking devices configurations due to which our network devices may not perform the appropriate tasks (i.e. the intended task for which the device is made or purchased), as a result even the harmful activities in and on the network may be shown as harmless network communication.
A firewall generally detects spoofed programs which are generally made to spoof some or any useful resources and thereby make an attack (Ex. Spoofed antivirus tools which are originally made to extract information from the network).
Due to the absence of firewall the intruders may install any spyware and there by the intruder can extract information like user name and their respective password of the user in the network.
Usually firewalls can scan the entire network for the available unnecessary open ports and security breaches inside the network to protect them from the outside world thus the absence of firewall usually help the intruders to intrude into the network.
As the firewall is absent in the network the intruders can easily intrude into the network and thereby the intruders can gain the access to well-functioning network devices
Mohamed M. Abd-Eldayem [4] has analyzed the Intrusion Detection System (IDM) based on Naı¨ve Bayes classifier. This technique identifies the most important HTTP traffic features that can be used to detect HTTP attacks. The main objective is to enhance IDS performance through preparing the training data set allowing detection of malicious connections that exploit the HTTP service.
Annie shebanow, Richard Perez et.al. [5] explores how use, misuse, positive and negative, obstacle, and abuse testing cases of firewalls have broadened the security policies that mitigate or prevent threats in a cloud environment. According to them when comparing the efficacy of different types of firewalls, the focus should be on the capabilities of the data-transfer layers and the position of the firewalls. It is best to use the four layers of the Transmission Control Protocol/Internet Protocol (TCP/IP), which work together to transfer data between hosts: hardware (data), IP (network), transport, and the application layers.
Chirag Modi, Dhiren Patel et.al. [6] has surveyed different intrusions techniques affecting availability, confidentiality and integrity of Cloud resources and services. It examines proposals incorporating Intrusion Detection Systems (IDS) in Cloud and discusses various types and techniques of IDS and Intrusion Prevention Systems (IPS), and recommends IDS/IPS positioning in Cloud architecture to achieve desired security in the next generation networks. Ehab Al-Shaer, Raouf boutaba et.al. [7] has identified different anomalies that could exist in a single- or multi-firewall environment.
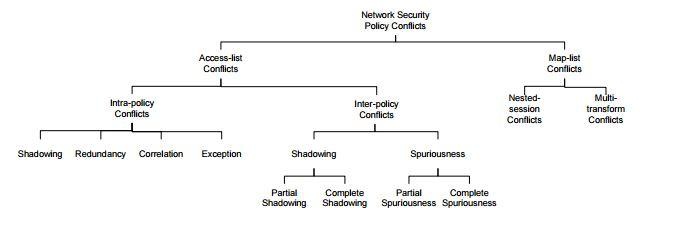
They also present a set of techniques and algorithms to automatically discover policy anomalies in centralized and distributed firewalls. Hazem Hamed, Ehab Al-Shaer [8] has presented a comprehensive classification of security policy conflicts that might potentially exist in a single security device (intra-policy conflicts) or between different network devices (inter-policy conflicts) in enterprise networks. Their approach is sufficiently general that it can be used to verify many other filtering based security policies such as authorization servers, intrusion detection, and intrusion prevention systems. Figure 1 shows the organization of their taxonomy for these conflicts
The following are the key constraints, which are to be kept in mind before designing a firewall
All incoming and outgoing traffic should pass through the firewall only. The traffic that satisfies with the local security policies should be allowed and the rest of the traffic should be denied by the firewall. Thus firewall should be placed at gateway position so that every data packet must pass through the firewall.
The following are the few key criteria used to choose the best firewall for an organization. I. Size of the organization Before designing a firewall any organization or institution must consider the size of the organization. In terms or networking size of the organization refers to a total number of network attached devices.
Before purchasing any firewall (hardware or software firewall) it should be decided, whether the organization can afford for such firewall (i.e. the cost of the new firewall should be balanced with the advantages it provides).
The maintenance of the firewall plays a very vital role in network perimeter security. The firewall maintenance should be as easy as possible so that it can be completely used for what it is made
Before purchasing or implementing a firewall it is mandatory to know what the firewall should protect, thus useful firewall can be implemented depending on our network resources and networking components. Any firewall can be considered as the useful firewall if it satisfies our local security policies and helps in making our security policies more efficient. Netfilter is a set of hooks inside Linux kernel. It allows kernel modules to register call back functions with the network stack in order to intercept and manipulate the network packet.
The Netfilter Hooks Generally there exist 5 types of hooks in kernel modules, these Netfilter hooks are listed below along with their functioning. When a network packet comes in, it is passed to the Netfilter’s first hook NF_INET_PRE_ROUTING. After that, the packet goes through the routing code, which decides where the packet is destined to, either another port in same network interface or another interface. It also might drop the packet if it can’t be sent.
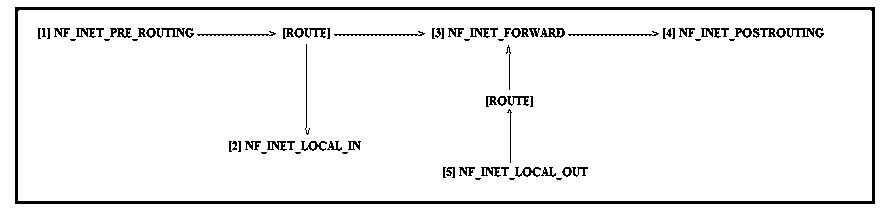
If the packet goes to another port in the same interface, the second hook NF_INET_LOCAL_IN is triggered. This happens before the packet reaches to the destination port.
If the packet goes to another network interface, the third hook NF_INET_FORWARD is called, followed by the fourth hook NF_INET_POST_ROUTING before the packet reaches wire again. There is one hook left, NF_INET_LOCAL_OUT. It’s called for local outgoing packets. Routing code is called before this hook to figure out the IP address and after this hook to decide the route. Kernel modules can register to any of the 5 hooks.
In this paper, we have examined firewall design thoroughly in an attempt to meet security and performance requirements of multitier applications. In all scenarios, servers hosting application components were separated from the company's corporate network used to conduct internal business, as an initial step to segregate resources with different security requirements. To tightly control interactions between the application's tiers, we looked at hosting tiers of the application on dedicated subnets. By deploying “PLUTO – A home office firewall”, we were able to significantly increase the difficulty of obtaining unauthorized access to sensitive resources from the Internet. At the same time, our firewall decreases the contributing to the cost of deploying and maintaining the infrastructure, and decreasing the likelihood that it will be misconfigured..
[1] Ravi Kiran Varma P, Valli Kumari V, and Srinivas Kumar S, "Feature selection using relative fuzzy entropy and ant colony optimization applied to real-time intrusion detection system," Procedia Computer Science, vol. 85, no. 2016, pp. 503-510, 2016.
[2] Ravi Kiran Varma P, Valli Kumari V, and Srinivas Kumar S, "Ant Colony Optimization-based Firewall Anomaly Mitigation Engine," Springerplus, vol. 5, no. 1, pp. 1-32, 2016.
[3] Free Computer tutorials. [Online]. http://www.homeandlearn.co.uk/BC//bcs5p4.html
[4] Mohamed M. Abd-Eldayem, "A proposed HTTP service based IDS," Egyptian informatics journal, no. 15, pp. 13-24, January 2014.
[5] Annie Shebanow, Richard Perez, and Caroline Howard, "The effect of firewall testing types on cloud security policies," International Journal of Strategic Information Technology and Applications, pp. 60-68, September 2012.